How Roaming fraud impacts your revenues?
Act faster in the identification of fraudulent roaming patterns
Roaming fraud is the best known fraud committed in the Visited Public Mobile Network by roamers and takes place when a subscriber moves from his home network to another operator network and uses the services with no intent to pay for it, making the home network responsible of its subscriber usage.
These type of frauds can be perpetrated in several ways, the most common are:
Fraudulent access to SIM cards from one or more service providers or network operators (subscription fraud);
Use of several operators within the same country with the purpose of maintain the network use below the threshold agreed between roaming partners;
Fraudsters take advantage of the time delay between the data interchange of the network operators to commit fraud;
Artificial generated traffic pump through high-tariff international numbers on small or remote countries, and international satellite operators, also known as International Revenue Share Fraud (IRSF);
How is Roaming Fraud detected?
The combination of several patterns provides additional insights into the roaming business performance
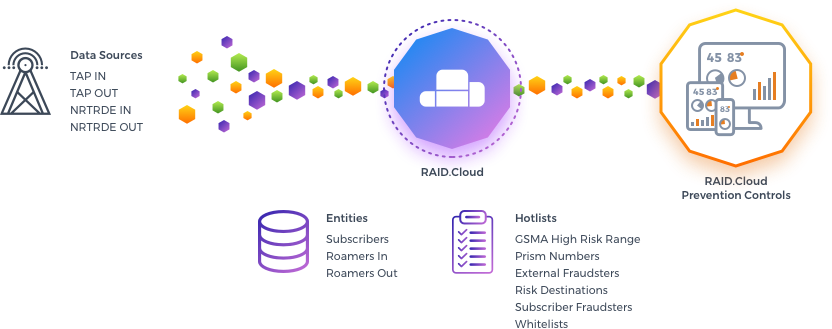
RAID.Cloud Roaming Fraud App, is an already pre-configured Fraud Management Application, which allows you to audit and control the Inbound and Outbound network traffic through the analysis of NRTRDE files in four distinct criteria:
High Usage Consumption
Identify and notify events with high volume of network traffic;

Traffic to known fraudsters
Identify and notify the events where at least an incidence of generated calling to a known fraudster number took place;
Risky Destination Countries
Identify and notify events where the volume of traffic generated is composed of numbers from an identified list of risky countries;
Risky Visited Countries
Identify and notify the events where the volume of traffic generated, is composed of numbers from an identified list of risky visited countries;
This information is captured in near-real-time, NRTDE files are created with a maximum delay of 4 hours compared with the traffic generated in the network, data is then ingested by RAID.Cloud and analyzed by our detection engines and risk hotlists.
Real-time insights into suspicious user activities
Network monitoring drastically decreases the timeframe fraudsters have to act, mitigating revenue loss.

Once the traffic patterns are detected and the thresholds higher than the defined ones, the solution raises the proper alarms presenting an dashboard with the detected fraud types (cloning, service abuse, IRSF, Interconnect Bypass/SIMBOX Gateway) that allows you to drill down and analyze more detailed information about the fraud pattern.
TM Forum Fraud Type
Service Abuse
Cloning
IRSF
Click to know more about IRSF. +View more
Interconnect Bypass/SIMBox Gateway
Click to know more about Bypass. +View more
Fraud Pattern
Abnormal Voice Usage, Abnormal Data Usage
Card Cloning, Risky Neighbor Country
Interpass Bypass, Risky Operators
Abnormal Service Usage, Risky Destinations, Risky Destinations through Card Cloning, Risky Neighbor Country Through Card Cloning, Traffic to known, fraudsters, Risky Operators, Risky Neighbor Country, Immediate Roaming
How do we identify and fight Roaming Fraud?
Near-real-time traffic processing unveils damaging behaviours
Improve business efficiency
Identify and thwart new methods of roaming fraud faster
Protects your revenues and company reputation delivering a competitive advantage through the detection of frauds allowing you to take the proper action to solve it;
Shorter time to market, register and start;
Increases revenue by eliminating roaming service availability limitations and making roaming more secure;
Improved customer experience using an accumulated understanding of fraud trends to only identify actual fraud incidents rather than “false positives”
Subscribe one or more apps and built your customized Fraud Management solution according to your needs and budget.
Real-time analytical analysis of network data
Use RAID.Cloud to hang up the phone on Roaming fraud
Next-generation services configured out-of-the-box to provide full coverage of Roaming Fraud;
Four ingestion methods available: manual upload, secure FTP on client side, secure FTP on RAID.Cloud and CIF mount point for inbound and outbound traffic;
Alarm management with a graphical dashboard and insightful email notifications, allows you to take instant awareness of all possible fraud types and behaviors with recommended mitigation.
Detailed alarm status provides to the fraud analysts the ability to perceive the scope of the alarm, but also to mark them if analyzed, helping them to manage their workload.
Detection engines that continually evolve based on the latest fraud trends;
Built-in Hotlist of know fraud numbers and countries provided according to GSMA recommendations;
Allows you to add records in Risky Destinations, External Fraudsters and Subscription Fraudster hotlists;
Whitelist of known customers with abnormal behavior already identified as non-fraudulent to skip the detection engines and reduce false-positives;
Control rules thresholds with near real-time alerts associated;
Network subscriber classification according to: activation date, type of market, customer risk and contract type;
Continuous upgrade to upcoming GSMA recommendations.