How is Subscription Fraud committed?
Evaluate your subscribers identity in near-real-time
Subscription fraud involves the fraudulent individual obtaining the customer information required for signing up for telecommunication new contracts or new services with a valid authorization but without any intention to pay for the products and services used. In this scenario, the service usage will creates a payment responsibility to the real customer.
Subscription Fraud it is just an enabler that allows the perpetrators to commit several different types of fraud. The impact of subscription fraud does not stop with revenue loss alone. The effects could be catastrophic in terms of escalating complaints, poor customer experience, dissatisfaction among support staff, and diminishing investor confidence and others.
The possible fraud scenarios that can be perpetrated are:
International Revenue Share Fraud (IRSF) - interconnecting payments for calls in roaming or off-net made using services or equipment's obtained with false subscription data;
Service Reselling - sells the service to other customer at below market rates as no payment will done to the service provider;
Commissions Fraud - dealers can gain commissions by simulation false services or equipment sales ;
Premium Rate Service Fraud - impossibility to collect the amount spend by the fraudsters in PRS calls;
Assets acquisition - buy new equipment's or services with a retention agreement with no intention to pay;
How can we detect Subscription Fraud?
Augment existing scoring models and know your customer (KYC) processes
Re-Enter in the Network
validates all the new services or contracts subscriptions, to identify and alarm the scenarios where the potential customer tries to enter in the network using subscription data that is similar to a known fraudster already added to a black list;
Multiple-Activations
validates all the subscriptions made during a period, one day, to identify and alarm the scenarios where there are multiple activations for the same entity with similar subscription data, even with no similarity with fraudster black list;
Social Activity (Fingerprinting)
based in the CDRs generated at the network switches, it will be built a social network for each entity based in the called numbers, cells used and other attributes, instead of observing the entity behavior, to identify and alarm the scenarios where there are common social network with an entity and a black listed fraudster.
How RAID.Cloud tackles Subscription fraud?
Friendly fraud prevention tactics, such as predictive scores, risk assessment, and linkage analysis
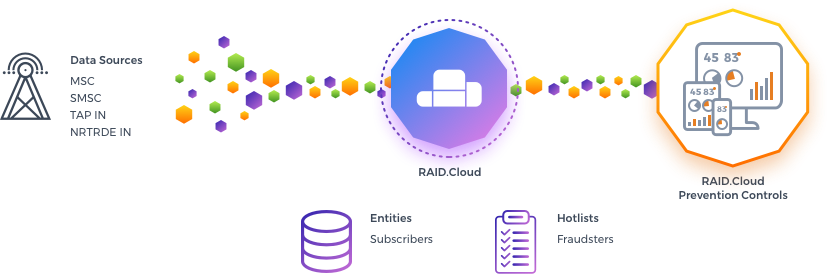
The Subscription fraud application contains only two engines based in analytics models (subscription), and another to build a social network (fingerprinting), with rules to detect attempts to re-enter in the network by fraudsters.
Subscription data similar to fraudsters data already registered in the black list;
Multiple activation with similar subscription data during a a certain period;
Incoming Social Network similar to fraudsters;
Outgoing Social Network similar to fraudsters;
Total Social Network, incoming and outgoing, similar to fraudsters;
Most significant cells used in common with fraudsters;
Suspicious IMEIs used in common with fraudsters;
Subscription Fraud App
What are you waiting to stop the mother of all frauds?
SCHEDULE A DEMO TRY NOWDetecting, Preventing, and Responding to Fraudsters at the entry point
Duel the priorities of customer experience while also stopping the flood of "never pay" accounts and chargebacks
Secure the access to your services
The importance of accurate identity in your business.
Protects your revenues and company reputation delivering a competitive advantage through the detection of frauds allowing you to take the proper action to solve it;
Shorter time to market, register and start;
Increases revenue by eliminating identity theft that can lead to reduced service availability limitations and making more secure the provisioning of services to customers;
Improved customer experience using an accumulated understanding of fraud trends to only identify actual fraud incidents rather than “false positives”;
Subscribe one or more apps and built your customized Fraud Management solution according to your needs and budget.
Take fraud detection automation to new heights
Meet the complete set of fraud management tools, built on a unified platform
Next-generation services configured out-of-the-box to provide full fraud coverage;
Four ingestion methods available: manual upload, secure FTP on client side, secure FTP on RAID.Cloud and CIF mount point for inbound and outbound traffic;
Alarm management with a graphical dashboard and insightful email notifications, allows you to take instant awareness of all possible fraud types and behaviors with recommended mitigation.
Detailed alarm status provides to the fraud analysts the ability to perceive the scope of the alarm, but also to mark them if analyzed, helping them to manage their workload.
Detection engines that continually evolve based on the latest fraud trends;
Built-in Hotlist of know fraud numbers and countries provided according to GSMA recommendations;
Whitelist of known customers with abnormal behavior already identified as non-fraudulent to skip the detection engines and reduce false-positives;
Control rules thresholds with near real-time alerts associated;
Network subscriber classification according to: activation date, type of market, customer risk and contract type;
Continuous upgrade to upcoming GSMA recommendations.