How is Bypass Fraud committed?
Deploy a multi-layered approach to grey routing traffic
Bypass Fraud is the most damaging and costly type of fraud that affect particularly countries where the cost of terminating international calls is much higher than a national call, but also on countries where international gateways are own exclusively by government carriers.
This fraud type as several scopes and can be recognized but the most common behaviors:
“Grey Routing” are arrangements where at one point in the route of a call an illegal action is taken so that even though both sides of the call look legitimate, although on the sending operator it looks like an international call, on the receiving operator it looks like a domestic call and settlement is done as if it was a local call.;
“Landing Fraud” occurs when a call is “landed” on a carrier’s network in a way that avoids toll charges. This is accomplished by making the traffic appear to have originated locally, or otherwise within the carrier’s network.;
“International Simple Resale” involves landing off-net calls onto an operator's network but avoiding the international gateway to avoid the International interconnect charges;
“SIM Boxes” involves several SIM cards (pre or postpaid which are more difficult to be identified) used to generate the maximum concurrent mobile calls possible;
The unavoidable reasons for the surge and persistence Bypass Fraud
Do you see fraud in your networks and your revenues are decreasing?
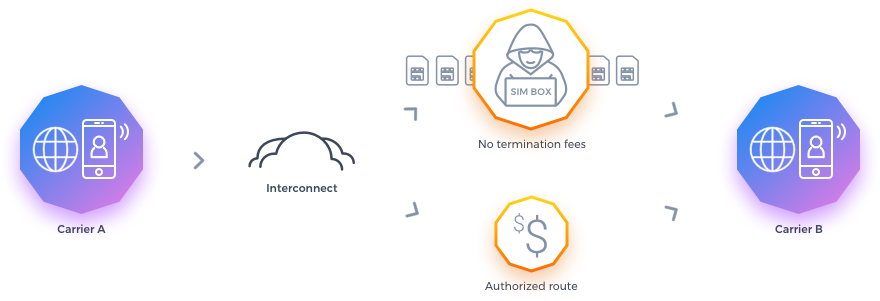
The Bypass fraud is the exploitation of immobile to mobile gateway equipment, typically called as SIM boxes to hijack inbound international calls while transferring them over Voice over Internet Protocol (VoIP) to the mobile network. As a result of this action, it re-injects the call back to the mobile network, thus terminating as a local call at the destination, creating a divergence making the carrier operators lose their call termination charges.
RAID.Cloud Bypass Fraud Application delivers an out-of-the-box solution to identify and recommend actions to stop these abnormal behaviors through the audit and monitoring of five indicators:
High Usage Consumption audits traffic, based in the CDRs generated at the network switches, to identify and alarm the scenarios where the traffic is high and with a B Number dispersion;
Long Term Usage audits traffic for a long period, be default a month, based in the CDRs generated at the network switches, to identify and alarm the scenarios where the traffic is not too high but there is a high B Number dispersion during the period defined;
MSISDN Swap IMEI audits traffic, based in the CDRs generated at the network switches, to identify and alarm the scenarios where there are IMEIs that are serving multiple MSSIDN in a short period;
Profiling audits traffic, based in the CDRs generated at the network switches, to identify behavior with deviations from a regular usage, in a particular period, when compared with the average of a previous period;
Advanced Fraud Detection using an unsupervised model with several indicators, based in the traffic generated at the network switches, identifying subscribers with a behavior similar to another entity already classified as fraudsters.
How do we identify and fight Bypass Fraud?
Stop fraudsters revenue and hinder their work
The bypass application contains several engines and for each engine different rules that will be used to identify possible fraud behaviors perpetrated by the subscribers or roamers inbound.
Our application delivers a service based on multiple layers of tracking, subscription-based access and security mechanisms in combination with Test Call Generator tests to confirm Bypass Fraud MSISDN cases, once detected details like fraudulent MSISDN, Route/Trunk Information, Call origination country, time of the test call made, the application can then initiate a dedicated and combined Traffic, Account, IMEI, IMSI, CCID, Location and Profile analysis, over the Subscription and Usage database available, to uncover the associated numbers.
A set of Detection Flows will run aggregating and evaluating the rules defined by the Fraud Analyst. Once the traffic pattern thresholds defined are reached, alerts will be raised. The data aggregation will be done per actor (MSISDN, IMSI, or other) according the segmentation and traffic considered. The data aggregation timeframe that will be used to accumulate the relevant events is One Day and One Month in certain engines. This ensures Fraud Analysts are quickly aware of customer airtime related activities which are breaking defined rules, thresholds and profiles in order to act fast in determining if the case is fraudulent.
Bypass Fraud
RAID.Cloud innovative approach can identify fraud in a matter of minutes
Start saving millions now!
SCHEDULE A DEMO
TRY NOW FOR FREE
What can i expect from RAID.Cloud?
Attack immediatly the unknown revenue loss from interconnect bypass or simbox activity
Decrease revenue loss due to call redirection, service inaccessibility and missing call backs;
Increase customer satisfaction maintaining service accessibility and quality standards;
Eliminate possible illegal national/personal security intrusion and route bypassing;
Eliminate hardware investment in tracking bypass equipment;
Shorter time to market, register and start;
Subscribe one or more apps and built your customized Fraud Management solution according to your needs and budget;
What is available to tackle Bypass fraud?.
Proven track record in automation and data analysis to detect fraud trends and accomodate new service offerings
Next-generation services configured out-of-the-box to provide full coverage of Bypass Fraud;
Configurable outgoing/incoming ratios for uneven outbound vs. inbound ratios present in Bypass Fraud scenarios;
Exceptions list (black and white lists of numbers, call types, etc.) to reduce the amount of false positives;
Profile matching of fraudulent MSISDN across existing active subscriber base to identify calling pattern cases;
Account level Analysis to identify the related connections;
Dealer identification to help tracing back the involvement of a Dealer in supplying bulk SIMCards for use in Bypass Fraud;
Route Analysis to identify the traffic origination (country) for more focused reporting;
IMEI analysis to identified the related connections from the equipment used to conduct Bypass Fraud;
Luhn check to reveal Bypass equipment’s with invalid IMEI;
Alarm management with a graphical dashboard and insightful email notifications, allows you to take instant awareness of all possible fraud types and behaviors with recommended mitigation;
Detection engines that continually evolve based on the latest fraud trends;
Continuous upgrade to upcoming GSMA recommendations.